The Myth of the Cyber Offense
Bottom Line: The Cato Institute draws from the historical progression of United States’ cyber capabilities over the past decade and their demonstrable effectiveness as decisive operations to argue for a cyber policy of restraint over a continued path to overreach.
The Cato Institute’s research and analysis present a quasi cost-benefit analysis for its readers to determine whether an escalatory cyber offensive has yet to prove its worth to the country in its coming age. Especially in this era of great power competition, should U.S. policymakers view cyber strength as a lynchpin or a crutch to the grand strategy by which America seeks to direct its foreign policy?
The key considerations (below) posed by Cato’s analysis take cyber strength and security out of the fictional realm so suited to its twenty-first century observers, and into the more consequential role it increasingly plays on the world stage. Is a potential “Cyber Pearl Harbor” such a far-fetched cry in the context of this analysis?
Track Record
Do cyber operations actually achieve stated foreign policy objectives?
Between 2000 and 2016, there have been 272 documented cyber operations between rival states – major operations involving thousands or millions of incidents. Of these operations, only 11 (4%) yielded a temporary political concession while 89 operations (32.72%) saw a retaliatory cyber response within a year. While the majority of retaliation was deemed low severity, nearly 30% were proportional, high-level responses. U.S. cyber defenses against continued Russia and Chinese cyber operations this percentage to respond in kind.
It’s important for the characterization of this data that most, if not all, of these active cyber operations partnered with USG government agencies to enhance their respective capabilities. In other words, many a cyber offensive starts to look more like strategic diplomacy or counterespionage than strictly cyber operations.
However, the data shows that, even when bolstering the operation with interagency coordination, the majority of cyber retaliatory responses have been short-lived – meaning they have not had a lasting impact on the rival state or actor targeted in the operation.
[Cyber] Grand Strategy
Cyber Command steps into the twenty-first century.
This data – representative of the latest shifts in the global playing field – has forced the United States to recognize that it now faces peer competitors in cyberspace and that all cyber adversaries intentionally and regularly strategize how to poke the U.S. cyber bear just enough not to spark armed retaliation.
These dangerous realities together inform an even greater one: that cyber campaigns of this nature, now involving peer rivals, have enabled our cyber adversaries to set the rules and norms of the game in cyberspace. They have taken away America’s upper hand, conceptually and operationally, according to the 2018 Defense Science Board, and others.
In an effort to reshape our strategic cyber framework to combat these challenges, U.S. Cyber Command launched in April 2018 a new cyber strategy that calls for persistent action to maintain cyber superiority. The USCYBERCOM strategy emphasizes the need for faster retaliatory responses to adversaries to keep pace with the constant competition.
However, Cato interprets the new policy as redefining cyber security through the lens of preemption, and placing offensive options before defensive strategic considerations. For instance, the new framework enables cyberspace more access into on-the-ground operations that may enhance the U.S. military’s access and movements, but doesn’t allow much oversight and coordination by the interagency process as the cyberspace of old.
Best Defense is a Good [Cyber] Offense?
Under what conditions could cyber operations result in inadvertent escalation?
Cyberspace has traditionally been characterized by a defensive posture, in part because the cyber track record is one of limited disruption like espionage and deception.
Open source information, such as the data cited in this study, does not depict the detailed ways in which China and Russia have been undermining American power in the cyberspace, though Cyber Command has repurposed the United States’ need to “contest dangerous adversary activity before it impairs [U.S.] national power.”
According to the Cato Institute, since 2018 our cyber policy has sought to go on the offensive against a target actor by demonstrating capabilities too superior to theirs to make the actor think twice about retaliation to escalate the conflict.
This rationale calls into question how re-shaping a national security policy around an offensive posture will affect the United States’ accountability in the cyberspace, and subsequently, stature on the world stage.
Cyber in Sum
Who owns the rules of the cyber game?
Since it is hard to define a victory, let alone a decisive victory, in the cyber realm, will this shift in policy blur the line over restraint? Externally, will an offensive U.S. cyber posture unintentionally escalate a conflict or signal unintentional aggression to foreign actors?
Alternatively, is cyberspace a different ball game? Should the U.S. be taking on a more offensive strategy to safeguard our sovereignty in cyberspace, so as to establish dominance that prevents intentional escalation and more by peer competitors especially?
All of these considerations, and more, are prompted by a deep dive into the Cato Institute’s analysis of the latest shift in America’s search for a grand strategy.
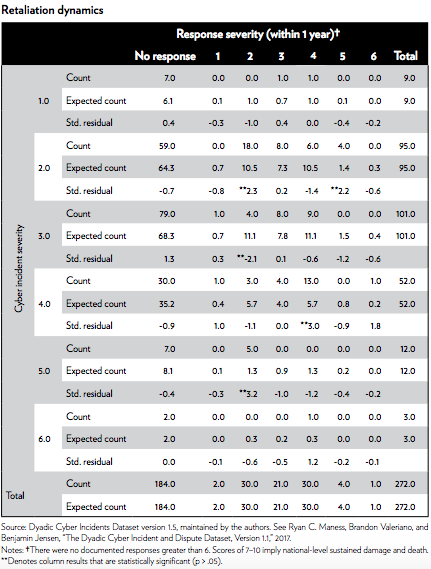
The data depiction of response severity of retaliatory cyber responses, conducted by The Dyadic Cyber Incident and Dispute Dataset (2017).
The Cato Institue study notes that retalitory cyber action is rarely severe, but U.S. defensive cyber actions against peer competitors has often prompted a proportionally severe retaliation to U.S. defenses, and occasionally, offensives.




